Cryptographic Hash Functions: Key to Digital Security

Cryptographic Hash Functions: how exactly do we achieve this? One of the fundamental tools used in digital security is the cryptographic hash function. These functions help secure everything from online communications to financial transactions. In this article, we’ll break down the concept of cryptographic hash functions, explain how they work, and look at some practical examples and applications.
What is a Cryptographic Hash Functions?
A cryptographic hash capability is a numerical calculation that takes an information (or “message”) and returns a fixed-size series of bytes. No matter how large or small the input, the output will always be of a consistent length.
Think of it like a digital fingerprint. Just as no two fingerprints are alike, no two distinct inputs should produce the same hash value. This unique feature is what makes hash functions incredibly useful for ensuring data integrity and security.
How Do Cryptographic Hash Functions Work?
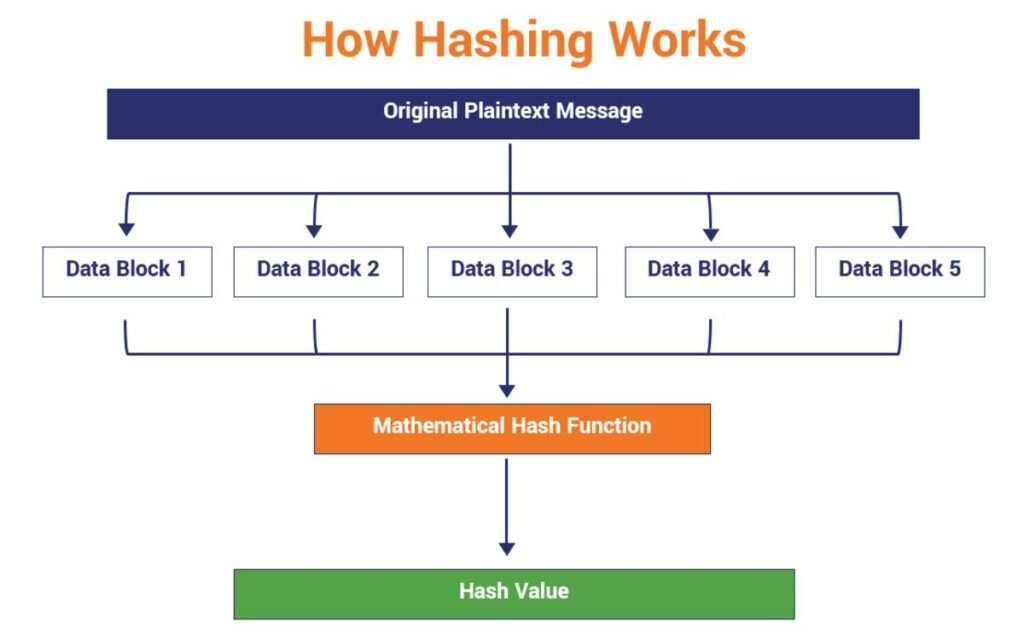
At a basic level, cryptographic hash functions work by processing data in a systematic way to produce a unique hash value. Here’s a simplified explanation:
- Input: The function receives an input of any length.
- Processing: The input data is divided and processed through a series of mathematical operations.
- Output: The result is a fixed-length hash value that is unique to the original input.
This process involves complex mathematical operations that ensure even a small change in the input results in a vastly different hash value. This property, known as the “avalanche effect,” is crucial for the security features of hash functions.
Key Properties of Cryptographic Hash Functions
To be effective, cryptographic hash functions must possess certain key properties:
- Deterministic: The same input will always produce the same hash value.
- Quick Computation: It should be fast to compute the hash value for any given data.
- Preimage Resistance: It should be infeasible to generate the original input from its hash value.
- Small Changes Produce Large Differences: A minor change in input should drastically change the hash value (avalanche effect).
- Collision Resistance: It should be extremely difficult to find two different inputs that produce the same hash value.
These properties ensure that cryptographic hash functions can effectively protect data integrity and security.
Examples of Cryptographic Hash Functions
There are several cryptographic hash functions, each with its unique characteristics and use cases. Here are a few prominent examples:
Cryptographic Hash Functions: SHA-2 (Secure Hash Algorithm 2)
SHA-2 includes a family of hash functions such as SHA-256 and SHA-512. These functions produce 256-bit and 512-bit hash values, respectively, and are currently considered secure for most applications.
SHA-3 (Secure Hash Algorithm 3)
SHA-3, the latest member of the Secure Hash Algorithm family, offers a different construction method known as the Keccak algorithm.
Applications of Cryptographic Hash Functions

Cryptographic hash functions have a wide range of applications, including:
Data Integrity
One of the primary uses of hash functions is to ensure data integrity. By comparing the original data’s hash value to the received data’s hash value, one can verify that the data has not been altered.
Cryptographic Hash Functions in Blockchain
Blockchain technology relies heavily on cryptographic hash functions. Each block in a blockchain contains a hash of the previous block, linking them together in a chain. This ensures the integrity of the entire blockchain, as altering any block would change its hash and break the chain.
Bitcoin and Hash Functions
Bitcoin, the pioneering cryptocurrency, uses the SHA-256 hash function as part of its proof-of-work mechanism. Miners solve complex mathematical puzzles based on SHA-256 to validate transactions and add new blocks to the blockchain.
Hash Functions in Password Security
When you create a password for an online account, it is often hashed and stored in a database. This means that the actual password is not stored, only its hash value. Even if a hacker gains access to the database, they only get the hashed values, which are extremely difficult to reverse-engineer into the original passwords.
Cryptographic Hash Functions: Salt and Hashing
To further enhance security, passwords are often “salted” before hashing. Salting involves adding a unique value to each password before it is hashed. This ensures that even if two users have the same password, their hash values will be different.
Integrity Verification
Cryptographic hash functions are essential for verifying the integrity of data. For example, when you download software or files from the internet, the provider often gives you a hash value. You can use a hash function to generate a hash value from the downloaded file and compare it with the provided value to ensure the file has not been tampered with.
Cryptographic Hash Functions: Challenges and Vulnerabilities
Despite their robustness, cryptographic hash functions are not immune to challenges and vulnerabilities. Some of these include:
Collision Attacks
A collision attack occurs when two different inputs produce the same hash value. While good hash functions make collisions extremely rare, they are still theoretically possible.
Cryptographic Hash Functions: Advances in Computing Power
As computing power increases, the ability to perform brute-force attacks on hash functions also increases. This is why older hash functions like MD5 and SHA-1 are now considered insecure.
Quantum Computing
The advent of quantum computing poses a potential threat to current cryptographic hash functions. Quantum computers could potentially solve the mathematical problems underlying hash functions much faster than classical computers.
Future of Cryptographic Hash Functions
The field of cryptographic hash functions is continually evolving. Researchers are constantly developing new algorithms and improving existing ones to address emerging threats and challenges. The transition to more secure hash functions like SHA-3 is part of this ongoing effort.
Cryptographic Hash Functions: Post-Quantum Cryptography
To prepare for the era of quantum computing, researchers are exploring post-quantum cryptographic algorithms that are resistant to quantum attacks. This includes developing new hash functions that can withstand the computational power of quantum computers.
Conclusion
Cryptographic hash functions are indispensable tools in the digital security toolkit. They ensure the integrity and security of data, from securing online transactions to protecting sensitive information. By understanding how these functions work and their applications, we can better appreciate their importance in our daily digital interactions.
Cryptographic Hash Functions: FAQs
1. What is a cryptographic hash function?
A cryptographic hash function is a mathematical algorithm that takes an input and produces a fixed-size string of bytes, unique to the original input, ensuring data integrity and security.
2. Why are cryptographic hash functions important?
They are essential for ensuring the integrity and security of data, used in applications like digital signatures, password hashing, and blockchain technology.
3. What are some examples of cryptographic hash functions?
Examples include MD5, SHA-1, SHA-2 (such as SHA-256), and SHA-3. Each has different levels of security and use cases.
4. How are hash functions used in blockchain?
In blockchain, hash functions link blocks together, ensuring the chain’s integrity by making it computationally impractical to alter any block without changing all subsequent blocks.
5. What is the future of cryptographic hash functions?
The future includes developing more secure hash functions and exploring post-quantum cryptography to address potential threats from computing power and quantum computing advances.
Read More: Complementary Currency